On the 31st of march 2021, Encryption Europe organized a webinar : « Encryption, cloud and GDPR – what is the recipe for survival ? ». This is the full transcription of the webinar. You may access the full video here : https://us02web.zoom.us/rec/share/uOyunqvaKz41CZxkBm3O7ob9ak8avbBESnSHRmYX5yqVei2PEeWRUFlYURdR41g-.9bJ3C9Wp2Z25TLBQ .The password is : T814u%^@
Encryption, cloud and GDPR – what is the recipe for survival ?
Webinar
March 31, 2021
- Eric Bedell – Chief Privacy Office – Franklin Templeton
- Xavier Lefevre – Founder& CEO – Fair & Smart
- Christophe Buschmann – Commissioner – CNPD
- Arnaud Laprévote – Founder & CEO – Lybero.net
- Jean-Christophe Le Toquin – Encryption Europe
As a transcription of a live event, this is spoken language and we hope that the reader will excuse all faults and imprecisions.

Arnaud Laprévote – Lybero.net
Initially, encryption was considered a good practice to protect data. Then it was integrated in industrial norms and finally it is becoming a legal requirement. GDPR is a core law in this regard, but there are others such as Eidas, Eprivacy, NIS, …

If you look at the text of GDPR, encryption is directly quoted in article 32 and in article 34. Article 32 relates to the security of processing, and 34 to the communication of data breach.



Fair&Smart is directly related to GDPR, but at the same time, Fair&Smart is also a data processor. Xavier Lefevre is going to explain us why and how Fair&Smart needs to deal with encryption.
Xavier Lefevre – Fair&Smart

Good morning, everyone. Fair and Smart is a SaaS software provider and, our solutions are designed to take care of all the visible aspects of GDPR compliance for our customers. What do I call visible aspects? It’s the aspects of GDPR and compliance which imply an interaction with the end user. It’s what we call privacy UX. It’s mainly three things : consent and preference management, GDPR rights requests, management and personal data transfers or acquisition. So our solution is labeled privacy tech. I know certification are also mentioned in the government as market guide. And in Luxembourg and Belgium, they are distributed by LuxTrust which is our exclusive reseller.

Next slide, please. Why did we choose encryption and why did we implement encryption into our solutions?
First, it’s obvious that contents are personal data. And they must be treated and managed as such and a consent management platform must handle all use cases. One of the main objective of implementing a consent management platform is to build a single source of truth, which will enable the data controller to know, am I allowed on or not allowed to run such a process on this data for that person, etc.. It means that you must be able to handle all use cases, including the one which may imply special categories of personal data like health data, etc. It means that security measures, appropriate security measures must be implemented.
And since we incorporated Fair and Smart in 2016 and GDPR was already known, even if it only came into force in 2018, we knew it and privacy by design was already a set rule. So we tried to take it into account and implemented the best we could.
And last but not least, there’s a strong market trend towards privacy and encryption, broadly speaking. So at that time, we decided to implement encryption because it makes us different from our competitors.
And also we anticipated that the level of security requirements would only rise in the coming years. And what is important is whether encryption is necessary for you. If you want to implement encryption, it’s really difficult to implement it afterwards and end to end encryption in particular. So it was really important right at the beginning to have that in mind and to to take it into account.
We act as data processors for our customers, who are data controllers, and most of them are big companies with DPOs, Cisos, and security policies. So it was also important for us to really take into account this security policies that were already in place. No, please.

So what were our issues and what are the issues regarding content management, broadly speaking?
First of all, we have some functional requirements. It’s to secure, of course, consent procedures and isolate the data of one of our customers from the data of other controllers and have a traceability of access. End to end encryption helps us to do that. It also makes it impossible for us to access to the data. It means that as a data processor, we only store encrypted data. We have no access to the keys. This is why we obviously cannot access the data.
Encryption thus raises security and minimizes risk both for our customers, but also for us as a data processor. And since like any data processor, we of course subscribe to cyber insurance, being able to show that we really implemented state of the art security measures is a very important aspect.
But end to end encryption is pretty complicated. And we were not experts at that time. This is why we chose carefully our end to end encryption provider. And what was important for us was the ease of implementation of such encryption process and also, of course, the support of the team. And this is what we found in the expertise of Lybero.net.
And, of course, there are financial issues like any software providers, the cost of the implementation of encryption has to be affordable for us and don’t put us out of the market. And, this is probably what make us, make that choice. It’s that « end to end » encryption is affordable now. It is not expensive. So I mean, it might be difficult in the near future for any data controller to say that they did not implement encryption because it was too expensive, because this is not true. So this is also one of the reason why we said, well, let’s do it.
Arnaud Laprévote – Lybero.net
So Lybero.net partnered with Fair&Smart and provided them a technology of encryption for web applications. Lybero.net is a cryptographic web software editor.
Lybcrypt is the core libraries in CryptnDrive which is an end to end encrypted drive and data rooms server. So these are our core values : ergonomy, security, intellectual property, simplified management, control. In Encryption Europe, there are many software and cryptographic software editors, we are all basically working on these kind of constraints for our customers. It is just that we have different use cases and different functions and many kind of software.
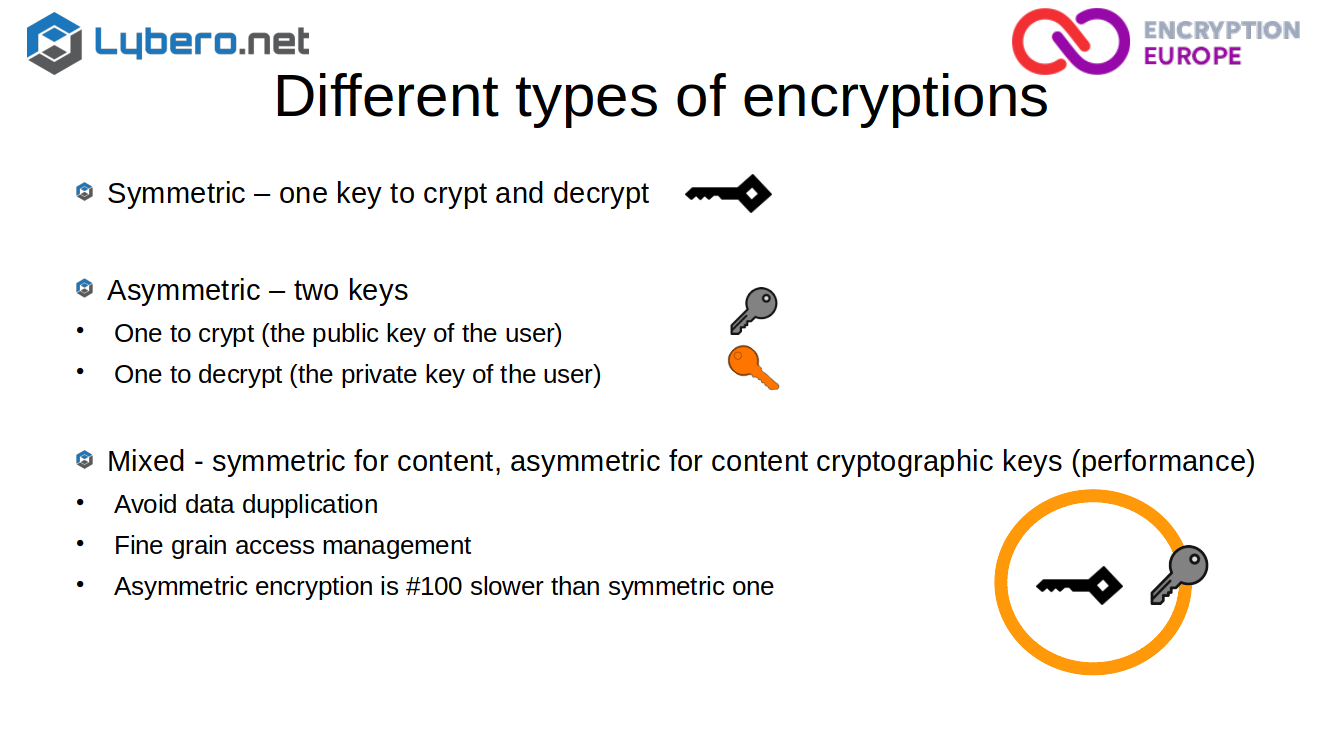
So to to come back to a little encryption, you have basically two types of encryption, the symmetric one and the asymmetric one.
Symmetric encryption means that you have the same encryption key to crypt and decrypt your content. Asymmetric one means you have two keys, one to crypt which is the public key, and one to decrypt the private key of the user.
Most of the time, in fact, you are using mixed encryption. Your content will be encrypted with the symmetric key and you will use an asymmetric key to encrypt the content key. The reason why is that first it avoids data duplication, you encrypt your content only once with one key. And for each person that need to access its contents, you crypt only the key. It allows also to have a very fine grained access management on your content. And the third thing is that there is a performance issue. Asymmetric encryption is around 100 times slower than symmetric encryption. So when you need to encrypt megabytes of content or kilobytes or gigabytes, you need to have something which is a fairly speedy so that’s the reason why mixed encryption is so used.
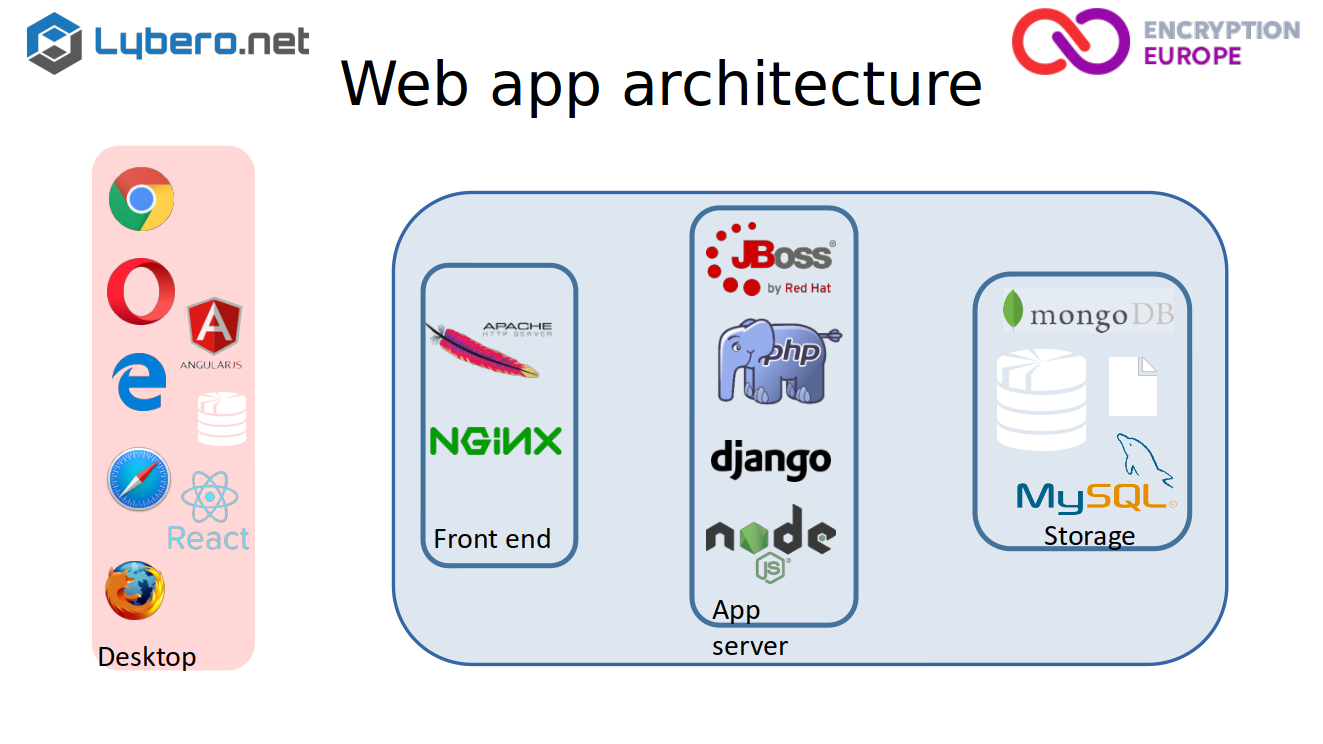
If you look at the architecture for web application, you have something like that :
• storage
• application server, using whatever language you want,
• and most of the time you have a front end,
• then you have your Web browser that will be used to to access the application.
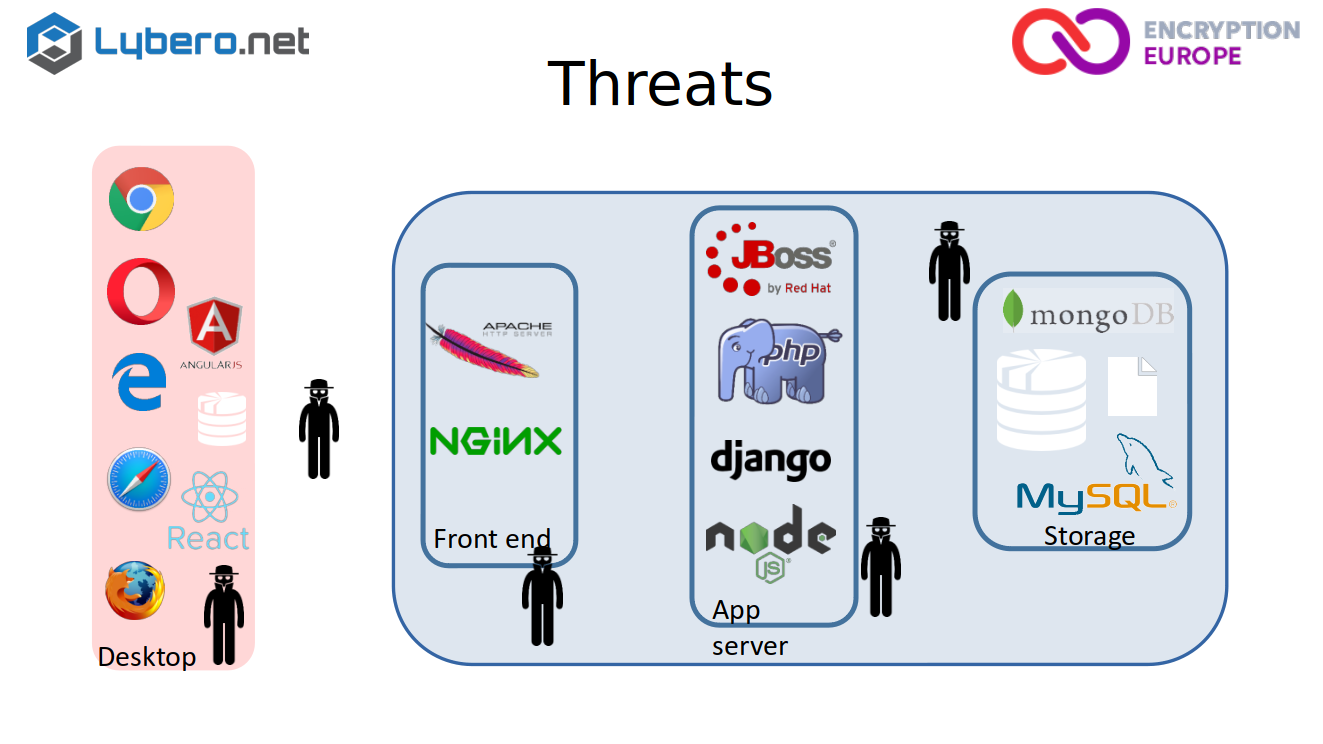
So if you look at the different threats, in fact, you have threats basically everywhere. Maybe if your attacker has access to the storage. Well, if it is not encrypted, you can access the data. If he can access to the application server, then he can grab the data, when they are going through or you can do the same thing on the front end.
Obviously, if you have an attack that is on the transmission channel between the server and the desktop. You can also grab the data or obviously on the desktop. So if you look at this schematic, what you see is that you have interest to encrypt as soon as possible because obviously you will lower the risk. If you crypt at the storage level, at the app server level or even at the front end level, you will have at least one problem, which is if an attacker has access to the platform, where’s the applications running? He can access the data. And it is also the case for the system administrator.
So really, I think that’s the key question you have to ask yourself when looking at a system : does a system administrator have access to the content? If the answer is no, OK, it’s good. If we answer is yes, then you have a problem, I think.
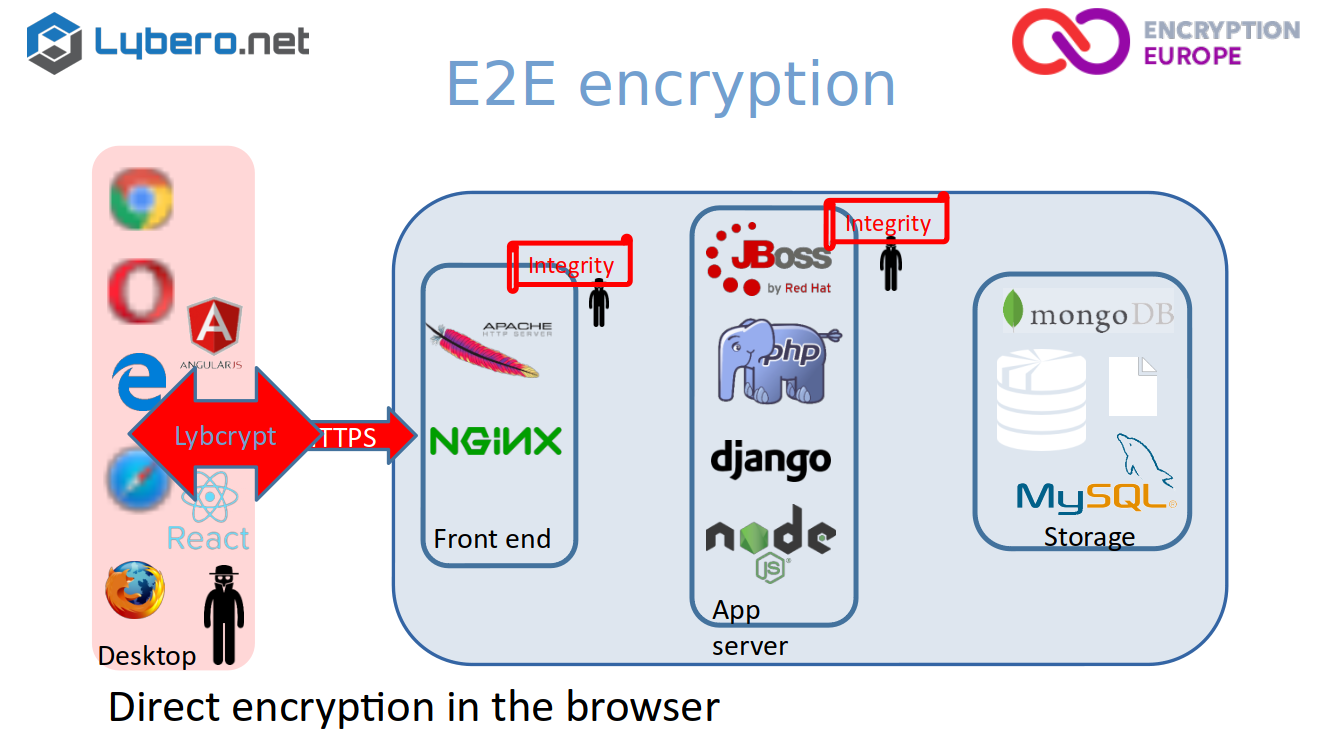
So what we do with end to end encryption is basically, for web application, you put the encryption directly in the web browser via the web browser before the content is sent to any server. So it doesn’t mean that you have no risk. It’s very obvious that if an attacker has access to your desktop, well, he has access to your data. So but what it does, he will only have access to your data and not the data to any of the other persons that are using the same application.
And here you have to take care of the integrity of basically all JavaScript libraries that you are using and sending to the web browser. The lybcrypt is just a library. And all cryptographic operations are done at the end, in the web browser on your desktop.
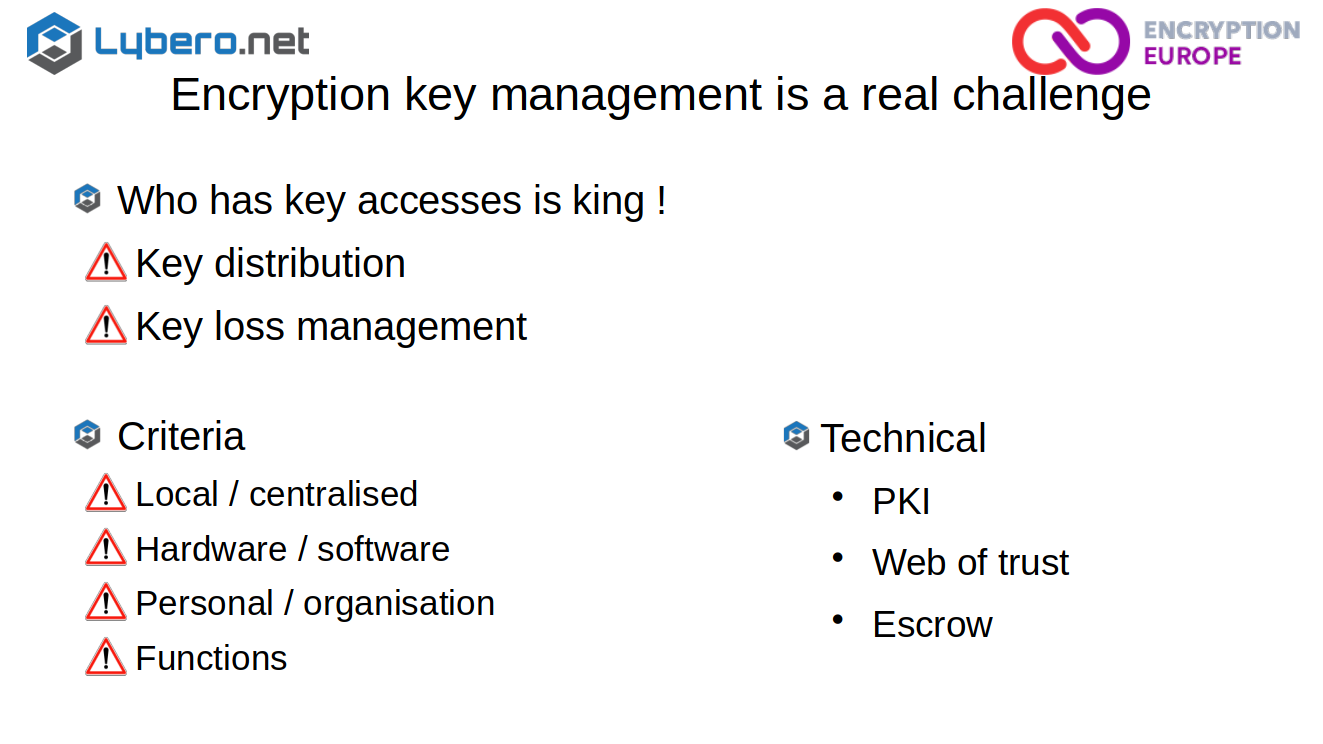
So encryption, it’s not so easy, but the real problem in such a system is the key management. And you have to be very careful on that, because the person or the persons that have the keys or that have access to the keys, can have access to your data. So what is especially touchy are the key distribution or creation and what does happen when there is a key loss. Well, when somebody loses its key, you have to do something.
The different criteria you have to look at are :
• is the key management local or centralized ?
• is it hardware or software solution ?
• Is it more something personal or is it more at the organizational levels ?
• and finally the different functions.
The first technical solution that you are seeing today is PKI. Meaning that you are going to centralize at least the public keys, and guaranty the integrity of the keys of each users via this centralized server. The second one is the web of trust. Each person is going to create the trust at his level and you are going to use this chain of trust to know that the key of somebody is a good one. What we use in Lybero.net is a web of trust, but associated with a centralized digital escrow.
Each content key is escrowed and when you need to release the key, you have a quorum based system which is highly secured and that allows to separate the authorization of access from the access and which guarantee that a single person as never the rights to access alone anything. If you need more details on quorum based escrow and threshold cryptography, please just contact me.
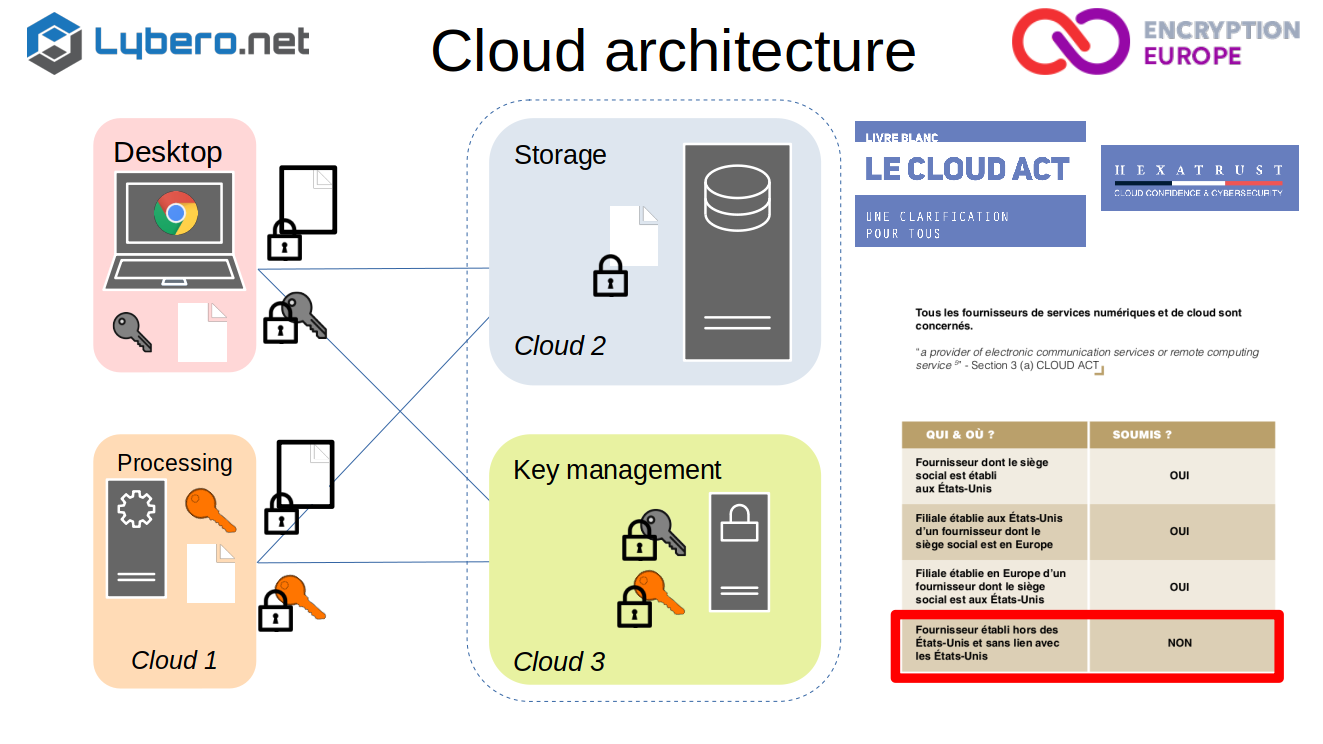
Let’s speak now of cloud architecture and encryption.
So what we see today commonly for cloud are architectures of this kind. So you have the storage on whatever cloud you wish, and it is encrypted. So it may be in a cloud provider at the same time, you need to have a key management server in one way or another. And the desktop will access these different elements on the application is going to run basically on the desktop, on your browser. But at the same time, you need to have processing. So the processing is a program that will run on a machine either in your IT system or on a secured cloud, but that needs to access the data.
As long as you don’t use homomorphic encryption (not really commercialy available), you need to decrypt the data to do the processing. So the key thing here is that to do the processing you need to decrypt the data and then you must be very cautious where you put that.
If you look at the nice white book on the cloud act of Hexatrust, you will see that the only companies that are not subject to the cloud act are the providers that are not established in the US and that have no links or whatever with the US. This has to be very carefully managed especially key management. The keys should be encrypted as soon as possible.

Jean-Christophe Le Toquin – Encryption Europe
Thank you. Now that we had the initial presentation on how Xavier and Arnaud, Lybero and Fair&Smart make the management of consent easy for the companies and secure, we are now going to listen to the perception or perspective from two people, from one professional who is Eric Bedel, CPO of Franklin Templeton, and from Christophe Buschmann commissioner at the privacy regulator of Luxembourg. And so, of course, we are not asking Eric and his staff to comment on the specific solution provided or delivered by anyone. But more on the other question of, why use encryption in the words of Christophe, when we prepared this meeting, he said the question is why not using encryption?
So first of all, I would like to head over to Eric Bedell. So Eric is a great example of an I.T. security professional who over his career broadened his scope and to become a DPO. I mean, frequently DPOs have a legal background and then it is a kind of natural extension to become DPO, which is still a very recent type of profession. And Eric is coming from the technical backgrounds and he has been awarded the title of DPO of the Year of Luxembourg last year. And one of the questions we will ask, is how much this has changed his life. But for the time being, Eric, what we would like to hear from you, I think, is because there are a number of DPOs with us today and privacy professionals. And so the question from your perspective is for you, how much encryption matters and and how do you make the decision to choose to support a solution which is encrypted or not? So what is the process and what are the benefits that you see in in selecting solutions which have a component which is encrypted? So really how it works in practical terms in your day to day work.
Eric Bedell – Franklin Templeton Investments
Good morning, everyone. So just quickly to answer to your question. It has changed a lot my life because now I’m talking with so many new people. My network has broadened a lot and I’m talking at many conferences. So that’s really what changed. I mean, my daily job has not really changed a lot with this title. But anyway, I’m really grateful to have received it, so thanks.
All right. So speaking quickly about the DPO role and expectations from a DPO, so what you have to do is really look at the risks. It’s all based on the risks. What it means is you need to use an impact analysis such as DPIA. You need to to do some sort of privacy by design reviews. You need to have records of your processing activities and you need to look at all the risks that are raising from that. You need to apply that to the scope of that you need to manage, that your company needs to manage in a way. So, for example, you do have some very sensitive information, some non sensitive information, but you need to link them compared to what you are doing with them. Like give you a concrete example. If you do have a list of emails from people participating into your marketing campaign, that’s not the same as dealing a list of email addresses of people participating into conferences around LGBT topics. Because the sensitivity is different about using the addresses for. So this is one part of the scope. The other part of the scope is really where your data is ? Is it internally in the company? In the cloud? Is it in the scope of your process or is it something that you do with an additional controller, for example? So you need to mind the scope and look at all the data and look at all the risks arising from those data in order to make sure that this is mitigated properly. You have different kind of tools that you could use. And this is really how the DPOs, most of us are doing it.
They consider encryption as being one of the tools that can be supplied to mitigate the risk arising from what I said before. So you do have, for example, the pseudonymization and you have the anonymization, but all of that are part of a complete set of tools that you can use. And again, depending on the risk, you may choose one or the other. I think encryption is really good because it is one, I would not say easy way, because I don’t know if it’s really easy for everyone and even more, as we said before, for DPOs coming from a legal background, it’s very technical, so it’s very difficult to understand. But as a tool in itself, it’s really good to think about it and say, OK, I do have a lot of risks to transfer that to a cloud platform and the only way for me is to use a very good tool. Again, cloud is quite good and it’s accessible everywhere, it’s very easy to use, but your data is in danger when it’s on the cloud. So then you need to think about, hey, what can I do to do it better? And maybe encryption is maybe the best way to mitigate that kind of risk using a cloud platform.
However, there are some discussions as well when you talk with the IT systems and the teams that yeah, OK, but if I am too much is going to be difficult to manage or my data is going to be difficult to manage, like it’s going to be difficult to back up some time. It’s going to be difficult to restore as well. It could be difficult to share with all the people that needs to get the view on the data so there are some some downside to it. So, again, I will just refer back to what I said at the beginning. You need to think about risk. What is the residual risk and how can you mitigated using the right tool? And encryption may be one of those tools. So that means you cannot or you don’t want to use it everywhere, but at the same time, you want to use it where it needs to be used and you really want to consider it.
Jean-Christophe Le Toquin – Encryption Europe
Thank you again. I would like a follow up question on this, which is the key message from from Arnaud, is that actually, the real issue is maybe not encryption versus not encryption, but rather do well the management of the keys. And and one thing we we also see are the benefits of the encryption and rather maybe from the encryption key management is the traceability of how people access or can access encrypted information. Is this something that plays a role in when you when you assess new solutions and you look at the integration of encryption into these solutions? I mean, how do you really I mean, put a focus or value the possibility to trace access of people to the data.
Eric Bedell – Franklin Templeton
So maybe to your first question, I mean, it’s really crucial when you and again, when you are a DPO, usually you are not looking at all the technical aspects that are related to encryption, like usually you have a CISO, or you have an I.T. team that knows about how to deal with it. But what is really important to say is the easiest it is to use, the better the tool will be used. You know, so if as a DPO you are advising the company to use an encryption, it needs to be easy to do. And again, if it’s on the cloud platform, if it’s software as a service or service as a cloud platform and so on, you want to make sure that this one is maybe already foreseeing encryption capabilities like it’s the privacy by design. So if you select a vendor or if you select a specific system, you want to make sure that this system is able to accommodate everything that is required by GDPR, including encryption or pseudonymization. So I think this is key to have a system that is working pretty well and easy to implement.
To the second question, the traceability is very important. So who is having access to my data is really central kind of discussions. Because of course that’s another part of the mitigation I was talking before. If the risk says, hey, this data cannot leave Europe, you need to make sure that data is not leaving Europe. And if you are a global company, it’s really difficult to understand who is having access to your data. Should there be someone, for example, maintaining the systems based in India or a system administrator that is based in India? Does he have access to your database or just to the system that is holding the database? And this is where encryption can be very useful for as well, because you are just sure by managing the keys properly that just the right people are having access. At least everything that has been declared or every people that has been declared are having access are really getting access to it and no more people are getting access to it. So that’s another way to use it.
Jean-Christophe Le Toquin – Encryption Europe
And that indeed, if people encrypt the data, but then you just have one sysadmin guy who has the one key that has access to everything and encrypt everything, then it’s not really super secure.
And that paves the way to Christophe, who is the commissioner, as I said, of the Luxembourg regulator. And again, a very interesting career with Christophe because you are coming from the technical background and you have been working for a global consulting company for many years. And then you actually switched to the other side. I mean, you spent a good deal of your career to help your clients navigate the fields. Now, you are now the commissioner that everybody now is terrified because you know everything from the inside. So how would you see the growing interest for encryption and do you see that I mean, we encrypt today differently from I mean, 10 years ago that one of the questions we have. And so when you see solutions I mean encryption. So how do you see it, especially in terms of compliance with the GDPR?
Christophe Buschmann – CNPD
Yeah, well, first of all, I don’t think it’s a question of two sides, so for all those who might be scared, I don’t think that there’s a justified reason because I don’t see this as a conflict between two sides, which needs to fight one another. And to get back to your question in regards of encryption. I would say, I take maybe a bit a broader view on the topic, because if I look at GDPR, which is my main topic, what is GDPR about ? GDPR It’s about governance. It’s about delivering on the promise, on giving people back control over their data on this promise. Obviously you can only deliver if on the other side, you know that the one who is in charge of this data has himself the control over the data. So GDPR, it’s about governance. It’s about risk management and how to handle data.
Now, this being said, if I look at encryption, I do see more advantages, and they have already been described, than just protecting confidentiality. I see it also and in a very important way also as a means as a preventive control on who has access to what and how can we make sure that this control is working effectively.
If you have a look at large organizations that are working on the day to day basis with huge amounts of data, with hundreds of processes and hundreds of services that they deliver every day. Now, one key challenge when it comes to managing governance at such an organization, it’s to be to control who is doing what with what and to be sure that they told you everything. Now, obviously, if you have, put encryption in place, not only as a measure to avoid a loss in confidentiality in case of a disaster, but also to be sure that only those who have a legitimate right to access data get the key to access this data. Then you have a huge advantage because your control is preventive. So you don’t have to chase people to find out what they are doing. But you can have this proactive role and make sure that that nothing happens, which should not happen. This is one one very important thing.
Now, if you look at a GDPR, I think Article 32 has been mentioned at the very beginning and encryption and also some other techniques have indeed been explicitly mentioned in GDPR. And GDPR is accountability based. So we should reason from the other side. So everybody should be in a position to be comfortable to explain why he did not consider those explicitly mentioned security measures in Article 32. I think that’s the more prudent approach. Now, you could say, well, I did not think of any reason why I should use it, but accountability is someone points you out specific techniques, at least think about why you could not do it. So that’s that’s one one key point I would like to make. And the other one is that GDPR, I mean, it’s a legal text. So it would not change, will not change every year, but it’s dynamic in its application, meaning that Article 32 explicitly states also that the level of measures that you put in place needs to take into account the state of art and the cost of implementation. And those two elements, they do change quite a lot. And as those two elements change, I think your assessment on what is appropriate needs to be adapted as well.
It has been mentioned, that the pure cost of implementing encryption, it’s not a valid excuse not to do it. I tend to agree now there has been an evolution on this as well over time. I would say ten years ago cost of encryption was different than today. So please don’t forget to take this dynamic into account when you do your assessment, because we as a regulator, obviously, we take them into account when we fix our level of expectation, when we do our investigation. So this being said, I think there’s not so much negative things you could say about encryption. However, I mean, in particular, if you have to deal with many problems and the technical ones are just some part of the problems you have to deal with on your daily daily basis. And I think Eric mentioned it, DPOs do have many, many other topics which are not technical of nature to deal with. Please keep in mind that encryption, it’s one part of the solution, but it’s not the ultimate solution which comes for free. And you say, well, today I encrypted everything in my organization and for the next five years, nothing bad can happen in my organization. No, I think it’s a good tool, as Eric mentioned, which can help you address some risks.
It comes with other risks, which is very often the case in risk management, that one mitigating measure creates other risks. In this case key management. It’s obviously the next step that you need to deal with to make sure that, first of all, the solution is effective. And secondly, it doesn’t create risks which you hadn’t in the first place. I would add at the third element, please don’t forget to make a surveillance of the security of the algorithms, of the technologies that you use. Because we know that by definition encryption, it’s working on a permanent strife on one against the other and who can break what at what point in time. So don’t miss the point in time where maybe you need to adapt. But that this being said, I think it’s definitely a technology which which adds a lot of value now.
And in the last sentence and I say this now in general terms, I mean, I was consulted before you mentioned it. And please be aware of the fact that new technology, it’s also always marketed and sometimes marketed, maybe a bit excessively aggressively in particular when it comes to passwords. And unfortunately, it’s very often the case for very technical topics that people would like to leverage on the fact that the one who could buy it, that doesn’t understand what the technology is below. If someone just tells you I sell you encryption, please sign here. And I would apply professional judgment because probably he did not do the due diligence to be able to claim that he effectively managed to encrypt the data.
Jean-Christophe Le Toquin – Encryption Europe
Thank you Christophe. That’s a very good point and actually, just for the people who don’t know exactly how we work out in Encryption Europe. In Encryption Europe, so in order to become a member, while you have to be a SME and provide service in this field. But there is a peer review and we ask to have also participation of the technical leaders of the companies. So I can tell you that it is difficult to assess even for ourselves, I mean, how much the solution is encrypted. But this peer review has a kind of a chilling effect on the applications. And I’ve seen a few companies that were wanting to apply and say, OK, good. I mean, we are going to just have to join. And then you will be assessed by your peers, and I tell you that sometimes I’ve never heard of people again. So it seems that the system works and also keeps us acting as a community.
One thing I would like you to hear from Arnaud and then from Eric, which is the point just before the one you mentioned on the buzzwords, which is indeed a reality. And people I have been talking about encryption is not enough. It is the the fact that on the positive side, we are in a dynamic situation, meaning the cost of implementing encryption gets down. Of course, you have to be careful of the way you manage keys, which is not really an issue in our case today with Fair&Smart, because this is just between Fair&Smart and Lybero. So that makes it very easy for the end users. But nevertheless, there is this issue of security, of algorithms and risk associated with algorithm being compromised. Arnaud how do you really deal with this ongoing threat and how do you mitigate it?
Arnaud Laprévote – Lybero.net
Well, that’s a hard question, but there are a few elements and first of all, well, you have different strategies concerning that. The base strategy is basically encryption algorithms were normalized. So you can rely on the normalization process. It was a competition. So if you consider symmetric encryption, for example, AES is a Belgian algorithm, but it was adopted as the standard for I think, US companies and especially banks and insurance after normalization by NIST. It’s also the case for RSA, ECDSA or ElGamal encryption algorithm was also normalized. So that’s a first strategy you can use. The second one is you can rely on efficient, high value research centers and researchers. So today, researchers are starting to use what is called formal techniques to evaluate the value of algorithms, especially the transmission of information on this kind of thing. So we benefited from that in our escrow system because it is based on formal research that were made on digital voting. So by Inria and CNRS. So that’s the second strategy, and after that, there is, I would say the standard monitoring of what is going on, peer review also test, external pen testing these kind of things that we do to ensure the quality of what we do.
Jean-Christophe Le Toquin – Encryption Europe
Thank you. I know there is a question on the chat and I’ll let you read it and ask for some clarification. I would like you to ask a question to Eric while others may also ask question, which is this dynamic evolution of encryption? And so you have a long I career in security. How do you see the importance of encryption growing for the work in cybersecurity? I mean, do you see that indeed much easier today than 15 years ago? You see, there is some kind of political momentum, so people really now are more interested. We had this massive adoption of end to end encrypted instant messaging applications in the past two years. So how do you see the evolution and the perception on encryption and how it is today implemented so compared to 20 years ago?
Eric Bedell – Franklin Templeton
Yeah, so maybe what I can say is that I’ve seen a huge shift into the solution offered by vendors and suppliers. So before you had to manage a solution yourself, like, say you had to take this solution and just decide if you want to encrypt it or not, like you had, for example, an Oracle database where your product was running on and you had to decide yourself if you wanted to encrypt this database or not, and what part of the database should be encrypted or not. This shifted a bit now to more packaged services if I can say. For example, you are taking a new human resources management tool, which is on the cloud, Saas platform. And then this one is offering encryption. I mean, that’s an additional price, of course, but it’s just like by default encrypted. Of course, it’s it is raising the questions of keys that we mentioned before. And I would not go back to that again and see who is having access to it and not. But I think you see more bundling up from the vendor side of the business. So I would say we see a greater adoption, even if I believe people are not fully aware that they are using encrypted methodologies.
I know, for example, that a lot of companies using WhatsApp and WhatsApp is by default encrypted, but they don’t know it. So I think if you think about it, companies are adopting encryption, but in a kind of manner at the end.
Jean-Christophe Le Toquin – Encryption Europe
And that makes me think about the question to Xavier, because Xavier you and your company, you are the one really engaging with the CISOs and DPOs. So you have to tell them, look, this is what I’m doing. This is how I’m helping to secure your data of your company. And this is why we use encryption. And you made the decision very early to implement encryption into your service. So did you and you have been I mean, providing your service company four years ago or even five years now. Did you see a change in the way people respond to the fact that you have implemented encryption into your service versus all the companies who did not? I mean, do you see this as a game changer now or more today than five years ago? What has been your your journey with the encryption?
Xavier Lefevre – Fair&Smart
Well, clearly, things are evolving. But there is, as far as I’ve seen, really a market trend, towards, more security, more privacy, and more encryption, at the end, because, again, encryption now is far more affordable than it used to be some years ago. So, of course, encryption is not the only security measure or the only security tool that has to be implemented. But, it is one of them and it is very efficient. So, as a data processor, we run processing activities on behalf of our customers. But, our customers need to demonstrate their compliance. They need to demonstrate that they take the appropriate security measures, et cetera. And we are here to help, and we have to make them feel confident, with the processing activities that we run for them. And this is the reason why, in my humble opinion, the highest level of security is better than the medium or lowest one, as long as you remain competitive on a financial point of view, this is it. And we’ve seen it. If you can choose between two equivalent services, one is secured and one is not, and they are both at the same price. You will definitely opt for the secured one.
Jean-Christophe Le Toquin – Encryption Europe
Thank you Xavier. We are getting close to the end. We’ll have an announcement for the next session next month. But before I do this, to conclude I think the question from wisdom would be a good fit for Eric. Why don’t we actually always choose for the most secure type of solution which has everything included. And that maybe a question you ask yourself every day. So what’s your take on this?
Eric Bedell – Franklin Templeton
So I would say first you need to think about the risk. And again, I am referring to that again, because it depends what you want to secure. If you want to secure the list of coffee vendor or coffee machine vendor, as you know, I don’t really know if it needs to be encrypted at the time because it’s just a loss of time and efforts and money at the end.
So if you do your risk assessment properly, you should put everything that is required to mitigate the risk to the places where it’s really meaningful to put the effort and money and value in. You want to protect what is really risky in your company and not protect the whole company.
And also, I must say that the perimeter of the company has really drastically changed in the recent years. You know, we have talked about cloud already, we have talked about outsourcing, controler, controler processing agreement, controler processor agreements. You know, this change a lot of things because the data that you want to secure is not just on your bases, it’s not just in your data storage. You also need to rely on some other people. We need to transfer data to some other people. So the perimeter has really changed. So it’s pretty important to think about it in a way : Hey, what is the most risky? Is it to have the data stored in a file cabinet or in a safe printed in the safe, or is it something that you want to transfer, like to the other side of the globe through five or six different processors? Well, maybe this is where you need to select exactly the state of the art security measures that you can. And GDPR’s like that. But there are many other regulations and laws that are saying the same. It’s based on the risk assessment. It’s all risk based. So as a DPO, you need to decide where to put the priorities. Of course, in the ideal world, we will be all protected for everything. But again, consider exactly what Christophe said before, when you put something to mitigate the risk, it comes with other risks very often. So that’s not as easy as that.
Jean-Christophe Le Toquin – Encryption Europe
Christophe, I would like to give you the last word, so because we are very lucky to have you and the regulator in this discussion. So I would like your conclusion on this. I mean, do you support echo what Eric says? And then I will. I will.
Christophe Buschmann – CNPD
I mean, it’s absolutely true. I mean, it’s at the end of the day about risk management and it’s about managing risks in the right way. Maybe just one element that I would like to add is that we should, I think, be conscious that there’s a huge difference between adding encryption on an existing process or infrastructure or organization or thinking about encryption since the start when setting up new processes. I think today, it is not acceptable that you don’t think about encryption for everything new that you set up that I honestly, I could not think about one single excuse. Why not to have a serious thought about this at that point in time now. When it comes obviously to making evolution of the existing landscape, the question is a bit more tricky. But and and I think the excuse not to encrypt it’s always present because to some extent it’s easier to find reasons why not to do something than to do it. And now I would like to stress out that if you stay for too long in such a position, you miss the moment where the benchmark over passed the level that you need to encrypt and you need to act in a hurry and you will have higher costs. Then if you take the opportunity now that maybe for some elements where it would not be strictly considered obligatory, you take the time that you still have to move. And I think that would be my recommendation if I could call it like this at this point in time for new things, please. It’s an obligation to have thought about it, but for existing things, don’t wait for too long. It will not necessarily be easy, but it would not be accepted in a couple of years and not to have a plan to move towards something equivalent.
Jean-Christophe Le Toquin – Encryption Europe
And thank you, thank you for this very strong and clear words, and it’s a perfect introduction to the next session, which will be on the 29th of April, same time also online. You can see the text on the Encryption Europe website. We will talk about legal interceptions of communications and the inextricable issue of back doors in encryption. And I think some people actually argue that, well, maybe it’s not such a great idea to implement encryption on existing and new services. And we will discuss this with Thimothée Rebours, who is the founder of SEALD, a member of our alliance. We have participants from EUROFIN and from the head of CIRCLE, the CERT of Security Made in Lu and its session will be moderated by Gregory from Encryption Europe, so my colleague. That’s will be in a month from now. And so we’ll discuss the other side. And that’s going to be quite an interesting session as well.
Thank you very much for this very rich session and thank you Arnaud and Xavier to introduce us to what you are doing. Big thank you to Eric and Christophe to having accepted to give your broader perspective as a CPO and the regulator. And I think this helps us really giving a very transparent and honest picture on the need of encryption in our solutions. So thank you for this and see you next month.

